Introducing ProxyAuth: The Security Gateway Built for Modern Infrastructure
Modern distributed systems need a smart bouncer at the entrance — a component that controls access, prevents abuse, and keeps applications lightweight and focused on their job. ProxyAuth is exactly that: a streamlined authentication and rate-limiting proxy designed for high-performance architectures.
The diagrams below illustrate three common deployment topologies where ProxyAuth plays a central role. The mission remains consistent: secure every request before it touches your application layer.
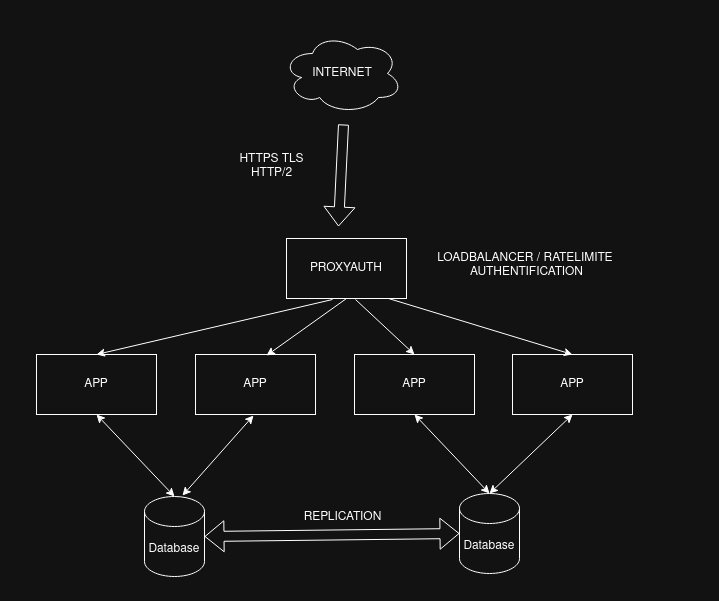
1️⃣ Direct Frontline Placement — ProxyAuth as the Public Gateway
ProxyAuth receives traffic directly from the Internet using modern protocols such as HTTPS/TLS and HTTP/2.
Once the request arrives, ProxyAuth validates identity, performs rate-limiting, and then forwards the authorized request to the appropriate backend application.
Data is stored across replicated databases so workloads stay resilient and scalable.
This scenario is ideal for:
• Microservices exposed publicly
• High-traffic APIs
• Environments without an upstream web server like NGINX
It keeps the architecture lean: fewer components, faster access control, tighter security perimeter.
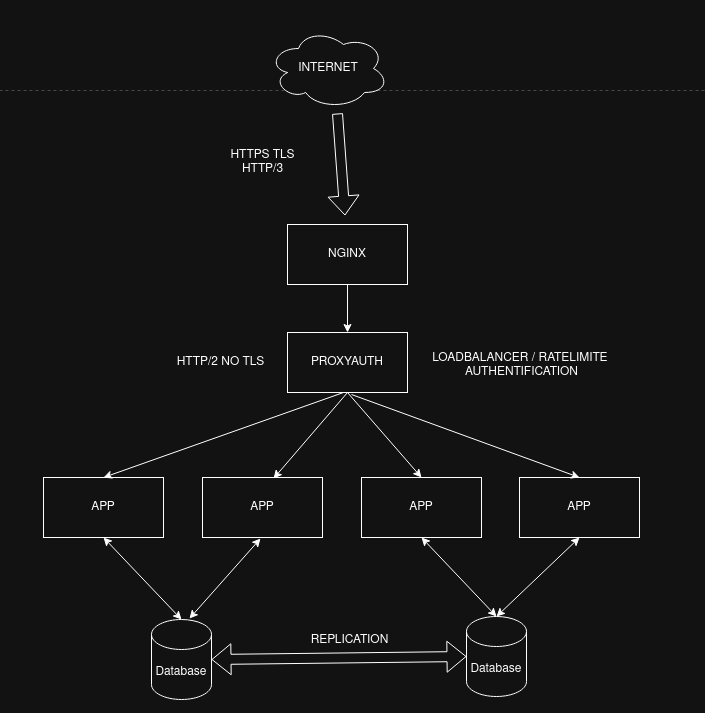
2️⃣ Behind an Existing Web Server — ProxyAuth Focused on Security Logic
In infrastructures where NGINX already manages TLS termination or HTTP/3 support, ProxyAuth takes place behind it, connected over HTTP/2 without TLS overhead inside the network boundary.
NGINX handles the networking complexity. ProxyAuth handles:
• Authentication
• Access control
• Rate-limiting
• Routing rules
This is a pragmatic choice when organizations want to enhance security and visibility without redesigning their stack.
Keep your current reverse-proxy — just make it smarter.
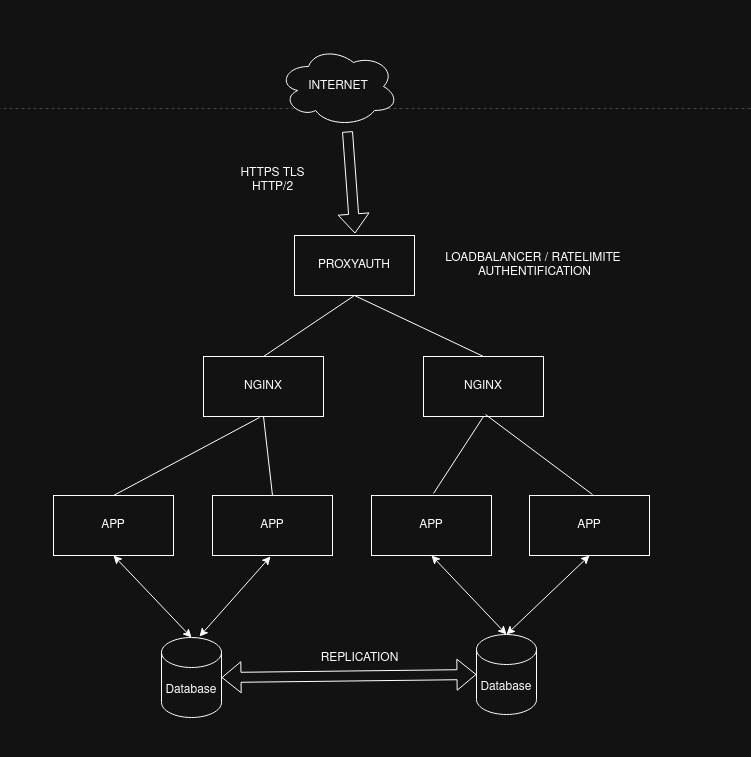
3️⃣ Distributed High Availability — ProxyAuth at the Security Edge
This final architecture demonstrates advanced horizontal scalability.
ProxyAuth becomes the unified access control layer, ensuring that every incoming request is authenticated before it reaches any frontend cluster.
Behind it, multiple NGINX instances fan out traffic across applications while maintaining performance isolation. Databases replicate to avoid single points of failure.
This setup is suited for:
• Enterprise and mission-critical workloads
• Multi-node clusters
• Progressive rollouts and zero-downtime scaling
ProxyAuth ensures that no matter how wide your platform grows, your security rules remain centralized and consistent.
A Simple Vision: Secure Access Everywhere
Whether deployed standalone, behind NGINX, or embedded within a distributed cluster, ProxyAuth provides:
• A single control point for authentication
• Transparent request forwarding to any HTTP service
• Reduced complexity in backend applications
• Horizontal scalability with no vendor lock-in
Applications keep their autonomy. ProxyAuth handles the gateway logic.
A clean separation of concerns — finally.